In this post, I want to cover specifically the narrow area of how to make your website GDPR compliant, and make recommendations for the specific changes you will need to be making.
What about Brexit and 2020… is GDPR still a requirement?
The General Data Protection Regulations (GDPR) applies to all companies based in the EU and those with EU citizens as customers. For UK businesses, the Brexit Withdrawal agreement won’t make any changes to the need to comply during the transition period, and nor will the requirements change for businesses who trade within the EU.
Furthermore, the UK is committed to maintaining the high standards of the GDPR ( and the government plans to incorporate it into UK law after Brexit.
The current GDPR regulations came into effect o 25 May 2018.
It is interesting to consider enforcement of GDPR regulations, and the GDPR Enforcement Tracker website provides s a list and overview of fines and penalties which data protection authorities within the EU have imposed under GDPR.
First, I have to say I am not a legal professional, and second this is a cursory analysis. At the time of writing, the database contains
- 16 cases of fines and penalties where the summary contains the word “web,” including a case in December 2019 regarding anoperator of a website for legal news had the privacy statement only available in English, although it was also addressed to a Dutch and French speaking audience.
- 5 cases where the summary contains the word “email,” including a case in 2019 where Vodaphone sent a marketing email to a large number of recipients (clients) without using the blind copy feature. The initial fine of EUR 60.000 was reduced to EUR 36.000.
On the one hand, this is not a huge number of prosecutions for non-compliance, but combine this risk with the increased sensitivity of personal data processing and awareness of this as an issue, and GDPR compliance becomes not just a statutory requirement, but also good business sense.
How does GDPR impact my website plans and functionality?
GDPR has a significant impact on website requirements, which will have a ripple effect on how your website integrates with your other digital activity like email marketing, social media, and e-commerce activities.
The golden thread that ties together all of these recommendations is that under the GDPR, the concept of consent being given freely, specific and informed is being strengthened, with new rules, which means businesses like ours need to provide more transparency.
Here are 10 steps you will want to review for your website, and discuss necessary changes with your web development team. Any questions, feel free to get in touch with me.
Let’s start with the straightforward changes that you will need to be making, and then move on to the more complex areas.
1. Forms: active opt-in
Forms that invite users to subscribe to newsletters or indicate contact preferences must default to “no” or be blank. You will need to check your forms to ensure this is the case.
As an example, the current Boots registration form pre-GDPR compliance ticked the opt-in box, forcing the user to actively opt-out. Very naughty, bad user experience, and must be changed by May.
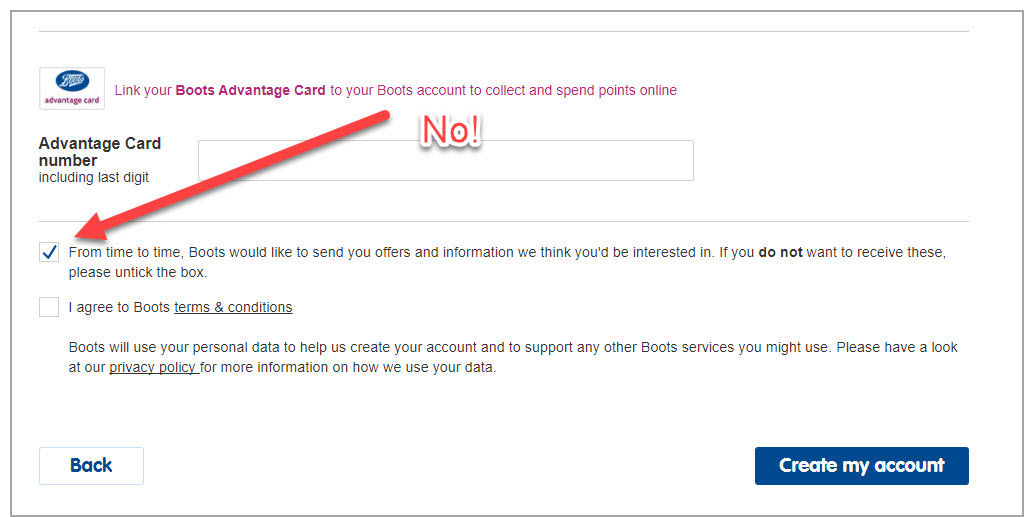
In 2020, that form has now been unticked as per GDPR requirements
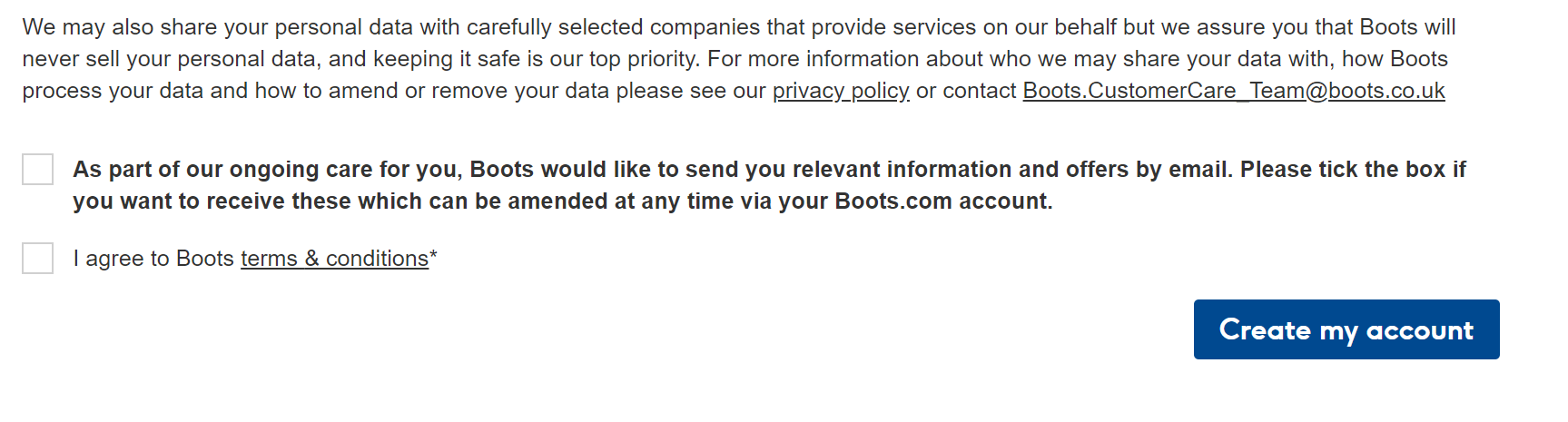
On the other hand, I would argue Sainsbury’s are not giving me a great experience by assuming an opt-in and forcing me to tick the box to opt out. I would argue they might be sailing close to the wind on that, and are definitely not delighting me as a potential customer:
2. Unbundled opt-in
The consent you are asking for should be set out separately for accepting terms and conditions, and acceptance of consent for other ways of using data.
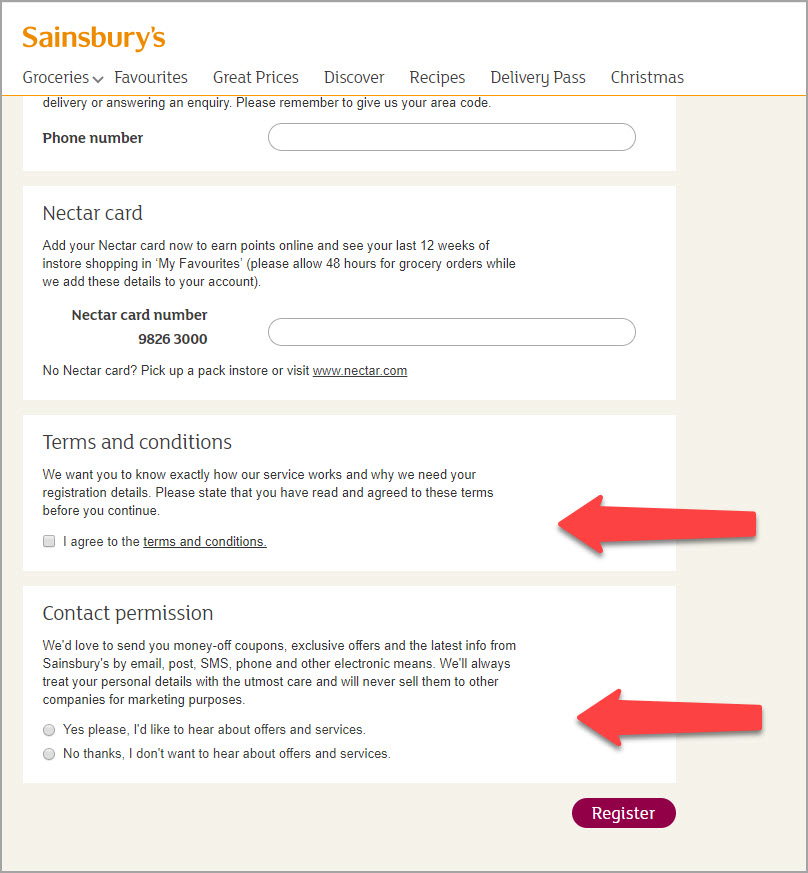
In this example, Sainsbury’s clearly set out the acceptance of their terms and conditions, and separately set out the active opt-in for their contact permissions.
It’s a shame Sainsbury’s didn’t get the option to be more granular in terms of communication opt-in preferences (email, SMS, post).
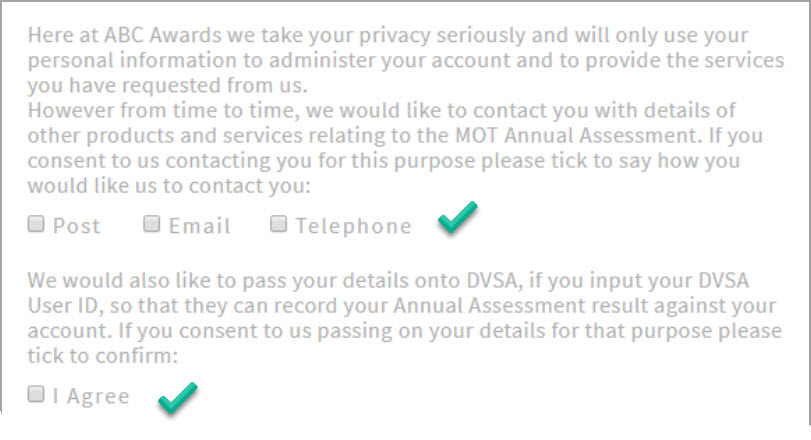
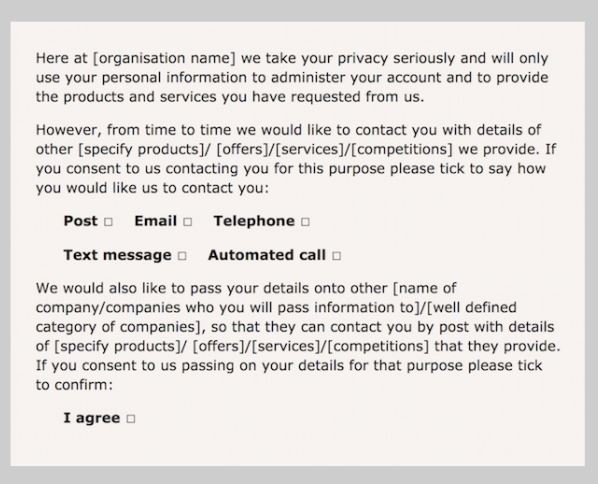
3. Granular opt-in
Users should be able to provide separate consent for different types of processing.
In this example, ABC Awards are asking for specific permission for each type of processing (post, email, telephone) and also asking permission to past details onto a third party.
4. Easy to withdraw permission or opt-out
It must be just as easy to remove consent as it was to grant it, and individuals always need to know they have the right to withdraw their consent.
In terms of your web user experience, this means unsubscribing could consist of selectively withdrawing consent to specific streams of communication:
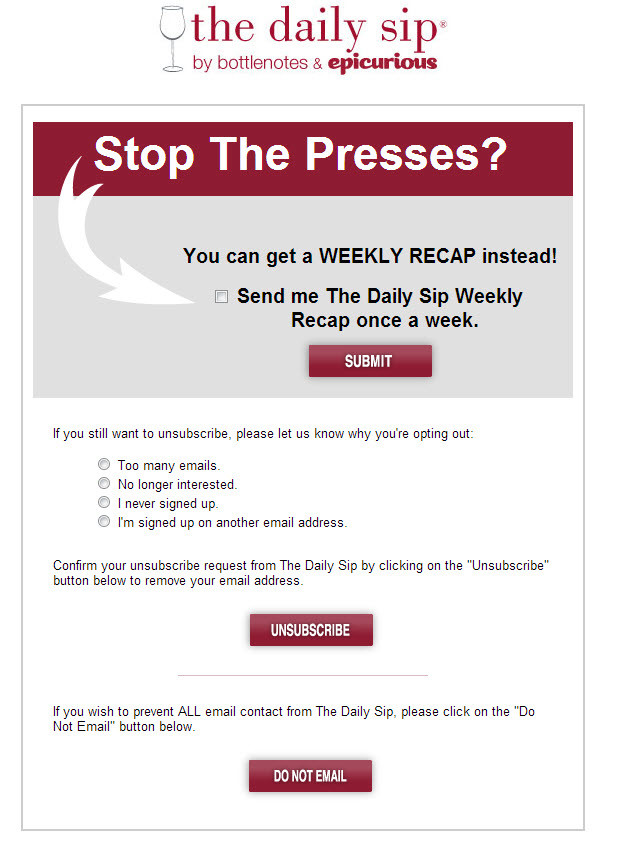
Or easily change the frequency of communication, or stop all communications entirely:
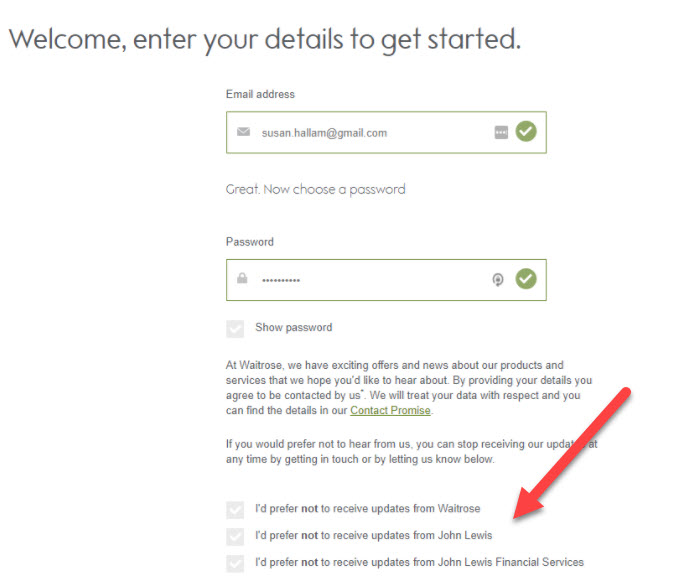
5. Named parties
Your web forms must clearly identify each party for which the consent is being granted. It isn’t enough to say specifically defined categories of third-party organisations. They need to be named.
In this example, you can see John Lewis understands the gist that we need to give named permissions for updates each from Waitrose, John Lewis, and John Lewis Financial Services.
Previously, the form asked users to opt-out rather than opt-in:
6. Privacy notice and terms and conditions
The Information Commissioner’s Office (ICO) has very kindly provided a sample privacy notice that you can use on your website. It is concise, transparent, and easily accessible.
You will also need to update your terms and conditions on your website to reference GDPR terminology. In particular, you will need to make it transparent what you will do with the information once you’ve received it, and how long you will retain this information both on your website and also by your office systems.
You will also need to communicate how and why you are collecting data. Your privacy policy will need to detail applications that you are using to track user interaction.
7. Online payments
If you are an e-commerce business, then you are likely to be using a payment gateway for financial transactions. Your own website may be collecting personal data before passing the details onto the payment gateway.
If this is the case, and your website is storing these personal details after the information has been passed along, then you will need to modify your web processes to remove any personal information after a reasonable period, for example, 60 days. The GDPR legislation is not explicit about the number of days, it is your own judgement as to what can be defended as reasonable and necessary.
8. Third party tracking software
Things now start to get tricky when it comes to third-party tracking software.
Many websites are using third-party marketing automation software solutions on their website. These might be lead tracking applications like Lead Forensics, Leadfeeder or CANDDI. Or they could be call tracking applications like Infinity Call Tracking or Ruler Analytics.
The use of these tracking applications raise some very interesting questions in terms of GDPR compliance, and in my opinion, this remains a grey area. At first glance, these applications track users in ways they would not expect and for which they have not granted consent. For example, it is tracking my behaviour each time I return to your website, or view a specific page on your site.
However, the suppliers of these applications assure us they are GDPR compliant.
First, the suppliers like CANNDI are advising that banners stating clearly and unambiguously that cookies are being used,
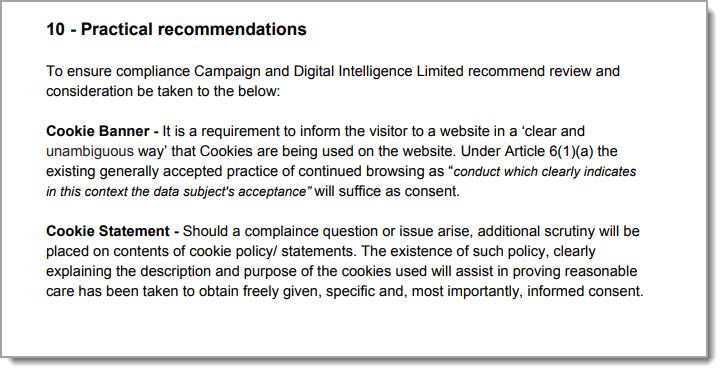
And, the software suppliers argue that the use of cookie tracking technology is in the legitimate interest of your business as a data controller, and specifically Recital 47 allowing for “processing for direct marketing purposes or preventing fraud.”
CANNDI advises:
Legitimate Interest - If using the legitimate interest principle within your website tracking it is advisable to have on record during your GDPR preparation that this is the case. This should include the grounds on which you are using this.
I want to thank CANNDI for sharing their GDPR perspective, and would recommend you read it (PDF.)

The providers of these tools are confident that they are GDPR compliant. But if the software is doing something illegal, then it is your business’ responsibility as the Data Controller. The real question is to identify the GDPR compliance risks in using this kind of software, and to mitigate your risks as a business owner. As a result, you need to review your contract with these software providers carefully.
9. What about Google Analytics and Google Tag Manager?
If you are interested in Google’s commitment to GDPR then a good place to start is this website: How Google complies with data protection laws
Many websites are configured to use Google Analytics to track user behaviour. Google Analytics has always been an anonymous tracking system. There is no “personal data” being collected, so I believe GDPR does not impact on its usage.
With regards to Google Tag Manager; it’s a powerful tool that enables your website to send information to third-party applications by inserting small amounts of code. You can integrate in-house data repositories, as well as external remarketing and retargeting systems, and a host of other services. The issue for businesses with regards to Tag Manager is to ensure you have a contract in place with the individuals that have access to your Tag Manager (which may well be your web designer, or digital marketing agency) to ensure they understand their legal responsibilities as a data processor on your behalf as data controller.
So, the underlying issue with the new GDPR is to identify and have in place contracts with your third-party data processors to protect both your own interests.
10. And finally… it isn’t only your website that needs to be GDPR compliant
The changes being introduced with GDPR will permeate your entire business, and in this series of articles, we are focusing purely on your digital marketing.
As you start planning the detail of your website, you will uncover an Aladdin’s cave of issues you will need to consider. The Information Commissioner has provided an excellent set of resources for your reference, but here are a few key questions to be considering now as we approach the May deadline:
- You probably have lots of personal data stored in various places around the business. Do you have a good understanding, and documented record of the data you hold?
- Do you need to either gain or refresh consent for the data you hold?
- Do you have a defined policy for how long you retain personal data, so you don’t retain it unnecessarily, and ensure it’s kept up to date?
- Is your data being held securely, keeping in mind both technology and the human factors in data security?
- Whether you are a data controller or data processor (or both), do you have the correct legal arrangements in place?






