WordPress is the market leader
WordPress is undisputedly the most popular content management system (CMS) for websites, with an impressive 59% of the CMS market share. It is also one of the most popular frameworks to build your website on, with nearly a third of all the websites on the internet built using it.
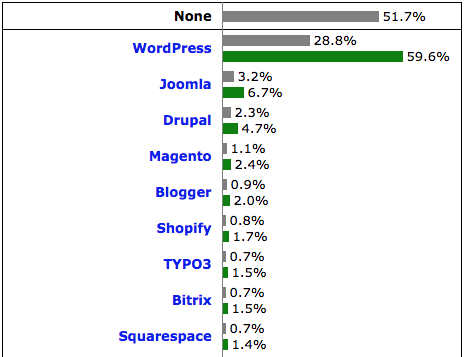
Source: https://w3techs.com/technologies/overview/content_management/allWordp
This popularity also has the effect of making WordPress a prime platform to target for hackers and other malicious users. A common question we encounter on a daily basis is “Why would anyone want to gain access to my website? I have no data of value to them”. Whilst this is definitely an understandable statement, it is the wrong mentality to approach the web with.
An unfortunate statistic is that the internet is severely lacking well-informed users, with only roughly 25% of users globally able to complete medium-to-high difficulty tasks. This leaves a worrying amount of users open to abuse from the minority of technically proficient users.
In this post we will go through some of the most common methods in which a website can be compromised, some of the reasons why websites get hacked, and what steps users can take to protect themselves.
How are websites hacked?
When someone hears the word “hacker”, the most common image is probably of a hooded man in a dark room in front of a monitor with a plethora of lines of code running down his screen. However, the (sad) truth is that everyday hacking is not that interesting. In fact, the most common hacks are quite simple in nature, and the people attempting to hack do not even have to be highly proficient.
Not all types of hacking stem from code either. Social engineering – also known as social hacking – attacks are still some of the most threatening ones. Common scam practices still apply on the internet and can lead to your website getting hacked. As this is beyond the scope of this article, you can read more about social engineering threats in this tripwire article.
Social engineering aside, the internet is still an unfriendly place for websites. Wordfence, a leading WordPress security plugin developer, releases monthly WordPress attack reports. From the September report we can see that the majority (91%) of attacks are actually brute force attacks.
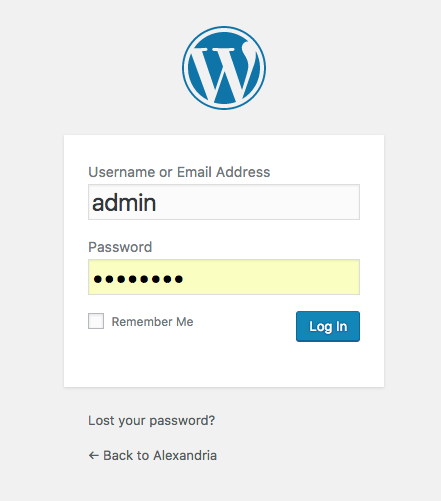
A brute force attack is a very simple concept. Anyone can try it, with usually no repercussions. On that note, why don’t we initiate a brute force attack right now? Simply Google your competitor’s site and try putting /wp-admin at the end of their URL. If you’re in luck, they are using a WordPress site. All you need to do now is put “admin” as the username or an email address you know they are commonly using, ie “hello@competitor.co.uk”. Then think of things they would use as their password: their names, their products, significant dates… and keep trying combinations. You are essentially commencing a brute force attack. Now imagine if you had access to a vocabulary of words and a script that automatically tries to log in using different combinations of usernames and passwords. There is a high chance for insecure accounts to be cracked this way.
With the simplest form of attacks out of the way, it is time to investigate a more elaborate kind of attack that tries to exploit common weaknesses in your website’s files. As many of you might already know, a WordPress site has a number of theme and plugin files it relies on. These also commonly rely on code libraries written by other developers. Sometimes – partly because of poor quality of code and partly because of innovations in the field of hacking – exploits can be found.
Hopefully, an ethical, also commonly known as a white hat hacker, was the one who found the exploit. Generally, right after an ethical hacker finds an exploit, the owner of the code is made aware, they make the public aware to mitigate any potential damage and then the owner of the code releases a patch to fix the vulnerability. In cases where a malicious hacker encounters an exploit, it can be months or years before it is made known to the public. In any case, after exploits are made known, they are added to vulnerability lists which are easily accessible over the internet on sites like this one.
There are also attacks directly aimed at the server. It is a very complicated and broad matter and this post will not go into any detail. However, here is an interesting article if you would like to find out more: How to Hack a Web Server.
Why are websites hacked?
We have now explored some of the ways a website can be hacked, but the question of why it was hacked still remains largely unanswered. Unfortunately, there are many reasons why a malicious user would target your website and they range from pure boredom to spreading viruses and illegal media all over the internet.
As pure boredom, whilst a genuine cause, is quite straightforward, so we’re going to move onto a more complicated one: advertising. There have been many ways to fall victim to ad injection attacks, as they are known. The concept is simple: you distribute your often malicious adverts on a genuine site to drive more traffic to your own. This can take the form of simply displaying the adverts on the site or in extreme cases, redirect all traffic to the hacker’s site. These adverts can then contain malicious code that leads to gaining control over a user’s machine or sensitive data.
Another common cause of hacking one’s website can be to simply deface it as part hacktivism. The causes of this type of attack are as varying as the groups who carry them out. We have had plenty of reports of “anonymous” defacing websites of people they do not agree with, and even ISIS deploys the same technique.
Unfortunately, not all hacks are visible and some can be quite subtle and difficult to track. For instance, if you are using your WordPress site as an e-store you might store your client’s credit card details or personal information. This is quite valuable to any hacker and there is a high chance they will not make their presence known so they can keep exploiting this information. In addition, as monetary gains from hacking a website can be quite substantial we even encounter websites hacked only to mine cryptocurrencies such as bitcoin.
How can I protect my site?
While all the exploits used by malicious users can seem overwhelming, there are some basic steps you can take as a legitimate user to protect your website. Here is a simple security checklist you can use:
- Keep your passwords secure: always use a strong password and keep it in a safe place. Do not use the same password on multiple sites. Update your password every two months or so.
- Never use admin or publicly available emails for your admin account
- Keep your website up to date: as mentioned above, known exploits are made public. If your website is using an outdated, vulnerable version of a plugin or theme, you are at risk.
- Use a reputable hosting company: shared hosting and hosting provided by an irresponsible company can lead to your website being hacked because another website on the same server was compromised.
- Only grant access to users you can trust: do not give access to your website to users who do not need it, or who you don’t fully trust. Not everyone needs to be an admin.
- Use a security plugin: similar to antivirus programs for computers, there are security plugins for WordPress. Two of the major ones are Sucuri and Wordfence.
- Ask: if you have a security concern or a question regarding your website, consult your developer.
In this article, we investigated some of the common methods and reasons why a website can be compromised. Hopefully with this information, alongside the security checklist, hacking will no longer seem like an almighty threat that’s ever-present on the internet.
Stay safe, stay informed!